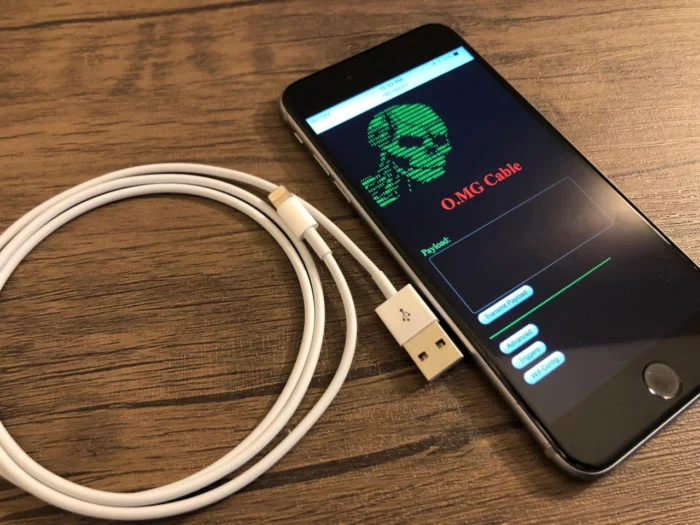
The O.MG Cable is an altered Lightning cable, absolutely the same as Apple’s original but concealing an ominous purpose: Once connected to a Mac, it allows a hacker to take control and do whatever he wants with a user’s computer.
![How a Lightning Cable Can Allow Attacks [O.MG Cable]](https://teknologya.com/wp-content/uploads/2019/08/How-a-Lightning-Cable-Can-Allow-Attacks-O.MG-Cable.png)
O.MG Cable, the Lightning Cable of Evil
The O.MG Cable ( “Cable Oh My God”) is a prototype made by the security professional (and hacker) known as _MG_ during DEF CON. On the outside it resembles a regular Lightning cable, while it usually works to transmit data between iPhone and a Mac (or other computer).
However, O.MG Cable has a number of additional components, including its own Wi-Fi network, which can be accessed by the attacker as long as he is close to the user with the compromised cable. Once connected to an iPhone or Mac, the hacker can send a series of commands and scripts to the gadget and do whatever they want.
Regarding the distance an attacker must have to access the computer compromised by the cable, with a telephone at a distance of 90-100 meters it is possible to interact with the device affected by the cable. You can also add an antenna to increase coverage or connect to a nearby Wi-Fi network, and through the Internet, control the victim’s computer from virtually anywhere.
On a Mac, you don’t even need an iPhone to be plugged into the other end of the cable; O.MG Cable allows a hacker to access the Terminal with full privileges, being free to collect any data or take control of the computer.
The hacker can even remotely “kill” the additional O.MG Cable implant through a “detonator”, erasing the tracks that might connect it to the attack, turning the evil cable back into a regular Lightning cable.
According to _MG_, the concept behind O.MG Cable is applicable to any type of USB cable, but he chose to demonstrate with the Lightning cable for one simple reason: Apple’s accessory is one of the best protected and secure there is. So if he managed to hack the apple cord, none is safe. The kit with the O.MG Cable and the “detonator” sold at DEF CON for $200 and, unsurprisingly, sold out.
What is the risk of an altered Lightning cable?
If a malicious professional manages to reverse engineer the O.MG Cable (given that it has been freely sold), it is no exaggeration to think that third party non-Apple approved cables can be sold directly to the end consumer in the future, with additional components that allow a hacker to take control of an iPhone or Mac, even if they need to be near the device.
At the same time, the technique could easily be implemented on USB cables for other types of gadgets, from Android phones to Windows computers, etc., with the same capabilities and potential to wreak havoc. With access released, an attacker can collect extremely sensitive data, inject keylogs, and capture what the user is typing (such as bank passwords and social networks).
Hackers can also send files that turn the PC into a zombie (botnet network) or dispatch ransomware and lock access to the PC, requiring ransom.
How to protect yourself?
The best thing to do is to avoid buying Lightning cables from unknown sources, especially if the product is not mFI certified, which enables the cable as Apple approved.
Every original or third-party cable that goes through apple scrutiny for safety and performance gets a “Made for iPod/iPhone/iPad” seal, which comes on the packaging. Always try to buy cables with this seal and from official retailers, even if it means paying a lot more for the accessory.

According to _MG_, the goal is to launch O.MG Cable as a product restricted to security professionals, as its own cable and not an alteration of an Apple Lightning, but it is a fact that not everyone can have good intentions when using such technology.
With info: mg.lol and Motherboard (Vice)