By now almost every day we receive messages that seemed to come from reliable sites but in reality they are not: a trick of cyber criminals to deceive users and get credentials to access accounts. Here are the Simple tips to recognize scam mail.

Phishing is the name by which cyber attacks are called which could arrive via email but also by other messaging systems. Apple users are targeted by cyber criminals who send e-mails and messages by sending messages that appear to come from real companies in order to steal login credentials to user accounts, for example by providing access to their Apple ID to attackers.
The attack methods evolve constantly and if at one time it was easy to recognize patently false messages, now the attacks are better conceived and exploit marketing techniques to deceive even experienced users.
How to protect yourself?
Scammers use phishing and various “social engineering” techniques to try to trick the user into revealing personal information, such as an Apple ID password or credit card information. It can happen via email, phone, text message or notifications that appear when we surf the web.
Scammers often use messages and notifications designed to appear to come from a company or a trustworthy person to try to trick us into sharing passwords, credit card information or other information. Phishing can come in the form of email, text message, a web page but also a phone call.
Signals that we are dealing with a phishing attempt
There are common signs of a possible phishing attempt:
- The sender’s email address does not match the name of the company from which it appears to be.
- The message was sent to an email address or phone number different from the one you provided to that company.
- A link seems to be reliable, but it guides us to a site whose URL does not match the company’s website address.
- The message begins with a generic greeting, for example “esteemed client”; in general, a company that contacts us for legitimate purposes uses our name in the emails we send.
- The message appears very different from the others received from the same company.
- The message requires personal information, such as credit card information or an account password.
- The message is an unsolicited message and contains an attachment.
- The call is an unsolicited call and the caller claims to be an Apple employee or service provider. Callers could use flattery, threats or high-ranking friendships to push you to provide them with information or money.
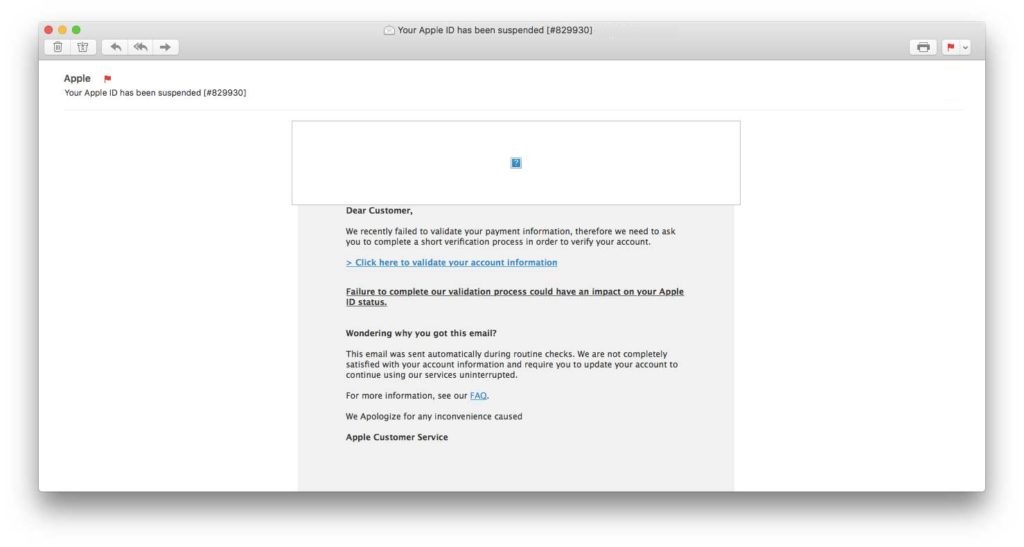 Another phishing attempt: the email would seem to come from Apple but in reality it is not so and the site on which you are hijacked has nothing to do with Apple.
Another phishing attempt: the email would seem to come from Apple but in reality it is not so and the site on which you are hijacked has nothing to do with Apple.What to do
Never provide information about your personal account, including your Apple ID password, credit card information or other personal information, by email or text message and use extreme caution when opening links in messages or sharing information on the phone. At our limit, we visit the company website directly or call ourselves.
- With the Apple ID it is advisable to activate two-factor authentication; in this way the password alone will not be sufficient to access the account.
- It is essential to use a secure password, keep an eye on notifications related to your Apple ID and keep your contact information always safe and up to date.
- Never share temporary verification codes with anyone, which Apple uses to verify our identity.
- Do not click on links in emails or text messages and do not reply to such messages without checking the sender. In case of doubt, go to the site of the company in question, find contact information and report the problem directly.
- Do not click on the links or buttons of a website without ensuring that the address (URL) of the company website appears to be correct; (on the Mac, you can move the mouse pointer over the link to view the URL in the status bar. If you can’t see the status bar in Safari, you have to choose “Show status bar” from the “View” menu; On the iOS device, just touch and hold the link).
- Do not open or save attachments from unknown senders. If you receive an attachment you did not expect, contact the company to check the contents.
- If we are not sure of the origin of a browser pop-up window, we avoid clicking on the links or buttons in the window.
- Always verify the identity of the caller before providing sensitive information on the phone. If we receive an unsolicited call from someone who claims to call on behalf of Apple, hang up and contact the company directly.
Report phishing attempts and other suspicious messages to Apple - To report a suspicious email, you must forward the message to Apple with the complete header information. In MacOS Mail, just select the message and choose “Forward as attachment” from the Message menu. These email addresses are monitored by Apple.
- If we receive a phishing email designed to appear to be from Apple, we need to redirect it to: [email protected].
- To report spam or other suspicious emails we receive in the iCloud.com, me.com or mac.com inbox , you must send them to [email protected].
- To report spam or other suspicious messages we receive through iMessage, we need to send them to [email protected].
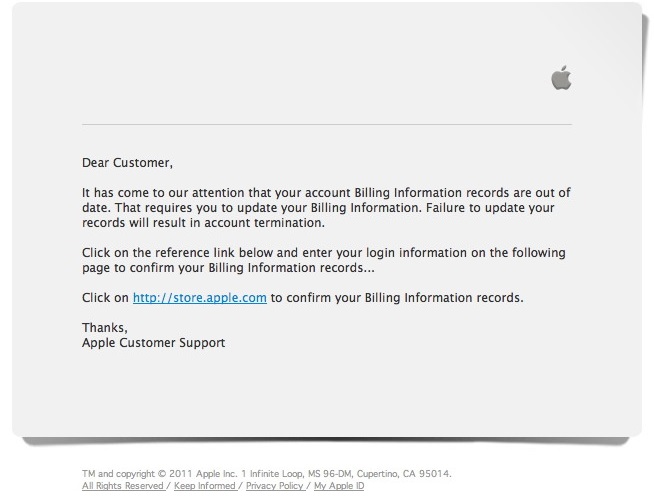 Another fake mail that would seem to come from Apple
Another fake mail that would seem to come from Apple